What is the best document security software to protect PDF documents?
There are many software products or solutions that you can use to protect PDF documents. But are they any good?
With countless PDF security solutions on the market, it can be difficult to discern which is right for your use case – and what price tags are worth paying. In this article we’re going to discuss the pros and cons of some of them so you can make a more informed decision.
PDF Password Protection
Adobe Acrobat, is the most popular software to password protect PDF files. However, there are many other PDF tools that cost less or are freely available. Like Adobe PDF, these tools can encrypt a PDF file and require a user to enter a password to decrypt it. Most allow you to add two passwords:
- one for opening the PDF document so it can be viewed
- one for applying restrictions or permissions such as editing, printing, and copying.
The main problem with PDF password protection however is as soon as you provide the password of a document to someone, the security of your PDF is out of your hands. The recipient can share the password and document with anybody they wish in a matter of seconds. Or they can just remove it in a PDF Editor.
Even if you have full trust in the receiver, tools and phishing methods are available to crack the password if someone gets hold of your protected PDF file – in other words users don’t even need the password to gain access. Elcomsoft for example, provide a PDF password cracker that breaks 40 bit keys in under a minute and uses GPU acceleration to crack 256 bit keys with brute force and dictionary attacks. It will also remove JavaScript, form fields and digital signatures.
There is no point in applying PDF restrictions because:
- they can be bypassed by using a PDF Viewer or application that just ignores them (e.g. Mac Preview, Google Docs, etc.)
- once a user knows the document open password then restrictions can be removed instantly using freely available PDF password removal tools
The only conclusion you can therefore come to is that they are completely useless.
Advantages of PDF password protection
- Cheap or free to use
- Ease of use – users usually have a PDF Reader installed already
Disadvantages of PDF password protection
- Once a user has been given the password to open a PDF they can remove it
- Hackers can break PDF passwords using cracking tools
- You have to use a really long and complex password to slow down hackers but this makes it harder for legitimate users to enter
- You have to find a way to securely transfer the password to authorized users
- PDF restrictions are completely useless since they can be bypassed or removed
- Online password protection tools require you to upload your sensitive documents to a remote server where they could end up being compromised or hacked
So, password-based encryption may be enough to slow a non-technical user down, but it does not provide any comprehensive protection.
Encrypt PDF files without Passwords, Securely Share and Control Document use
Plugin-based PDF Protection
If you need more controls than the basic ones provided with Adobe Security or other PDF editing tools, the natural place to turn is a plugin. The advantage of a plugin is that it can integrate with existing PDF Readers (usually your browser or Adobe Acrobat Reader), purportedly providing a seamless and easy way to enable more complex DRM restrictions.
Unfortunately, the implementation of these plugins often isn’t as simple as is billed. While installing a plugin is much the same as installing an application (users need Windows Admin Rights and their firewall needs to be configured to allow communication with a licensing server), plugins that interact with the same content can conflict with each other, causing unexpected behavior or breaking controls entirely.
It’s incredibly time-consuming and difficult for suppliers to test their plugins with every different combination of the most popular plugins, so many don’t even try. For the few that do, there’s no standardized testing process, and every time the application is updated (or a plugin for that application) then you are back to square one again.
Further, every plugin you install to your browser or application is another potential avenue an attacker can exploit. A vulnerability in a single plugin can result in a user’s system becoming compromised with malware – something you may not want to be held responsible for.
So, plugins have their flaws. But, even if you put in the time to work around them, are they effective PDF DRM tools? Unfortunately not. Even plugins built specifically for the Adobe Acrobat app with “Adobe certified protection” are not guaranteed to work or be safe. As anybody can write a plugin for Adobe Acrobat, it’s possible to create a plugin with a forged signature that can remove modification restrictions, DRM schemes, and digital signatures.
Advantages of PDF plugins
- Integrate with existing software
Disadvantages of PDF plugins
- Users need Admin Rights to install them
- They can easily break when an update occurs to the application or another plugin
- They can conflict with other plugins
- They often require users to reduce the security of their device for them to work
So, it comes down to this: a well-implemented plugin does provide better document protection than the default Adobe PDF security, but it won’t stop a determined attacker. It also does so at the cost of potential stability and security issues. If an attacker manages to compromise a user’s system with malware, the damage will be far greater than what a leaked document can cause.
Secure data rooms
What if, rather than attempting to secure PDF files directly, an organization instead creates a ‘secure’ environment that uses login/password-based access controls? This is the proposition behind a solution that is rising in popularity: the secure data room.
Rather than using their own infrastructure, companies can use the server infrastructure of their data room provider to quickly provision a data room and upload the necessary documents they want to share.
Advantages of Secure Data Rooms
- Users can access documents in their browser without installing any software
- They are quick to setup
- Additional restrictions can be applied to PDF files such as expiry
- Users and documents can be instantly revoked
Disadvantages of Secure Data Rooms
- User can share login credentials with others
- Multiple users can log in at the same time with the same credentials, making identifying a compromise difficult
- IP address logs cannot be relied upon since users regularly change their IP or can share the same one with others by using VPNs and proxies
- They don’t stop screen grabbing applications so users can take high quality screen grabs of document content.
- If printing is enabled, users can print to a file driver (e.g. a PDF printer that creates a digital document) rather than a physical one, thus removing all security
- You have to upload unprotected documents to a remote server
- Once you upload your documents to a remote server, security is out of your control. You’re entirely dependent on your provider to make sure unprotected temporary files are not left exposed
- Secure data room systems use JavaScript to enforce their controls, which can be modified by plugins or manipulated directly by the user in the browser’s developer mode to disable or remove it
- You are tied into paying a monthly subscription
- Costs can quickly mount up as you add additional documents and users to the system
So while secure data room systems do provide an additional level of security over PDF password protection, they also have many flaws and can be very expensive in the long term.
How to Securely Lock a PDF from Editing, Copying, Printing and Stop Sharing & Piracy
Enterprise Rights Management (ERM) systems
ERM systems such as Adobe Rights Management, are a worthwhile solution if you’re looking to protect documents for internal use. However, they are usually very expensive, and resource-intensive – you need to have an IT team in place to deal with the complex PKI-based setup and the requirement for admins to manage certificates (create, distribute, backup and revoke) and document use policies.
Key management also becomes an issue once you start to use it outside of the company, since you need a user’s certificate (public key) before you can protect documents for them. If you are looking to sell revenue-generating content in PDF format then this is a non-starter.
Advantages of ERM systems
- Can provide document collaboration
- Often support a wide range of file types
- Provide a full range of DRM controls
- Provide stronger protection than password encryption and secure data rooms
Disadvantages of ERM systems
- Complex to setup and maintain
- Need dedicated personnel to administer the system
- Does not work well with external parties as you need their certificates before you can protect PDF files for them
- Expensive
PDF DRM security
PDF DRM solutions encrypt PDF files and apply DRM controls to determine how documents can be used by authorized users (e.g. whether they can print it, edit it, etc.). They provide the strongest possible security for the protection of PDF files.
To properly protect PDF documents from leakage and theft you need a PDF DRM solution that:
- does not use passwords
- locks PDF files to devices so they cannot be shared
- provides transparent key management
- enables you to restrict PDF use
- prevents DRM controls being easily removed
- provides PDF expiry and instant revocation
- enables you to protect PDF files on your computer
- is easy to manage
A word of warning: Do not purchase a PDF DRM system that forces users to enable JavaScript in their PDF Reader or that makes them disable security functionality in order for their product to work. Doing so will put user’s systems at risk from security exploits and hacking. If their computer is compromised by opening a malicious PDF file, they might well be looking to sue you as a result.
The leader in the PDF DRM market is Locklizard, who has been providing US Gov strength PDF encryption with DRM controls since 2004. Here we explain how their PDF DRM software works and why it has the best features to protect your PDF files.
Locklizard Safeguard PDF Security
PDF encryption without passwords or certificates
Locklizard does away with the need for passwords or certificates. It uses transparent key-based security – there are no keys to manage or distribute to users. Decryption keys are automatically and securely transferred to authorized users’ devices and are stored in an encrypted keystore that is locked to each device. User’s never get to see these keys and if they copy their keystore to another device it will fail to open. This ensures that if users share protected PDF files with others, they cannot be opened.
PDF Restrictions & DRM controls
Locklizard enables you to apply PDF restrictions that cannot be removed by password crackers or PDF editing software.
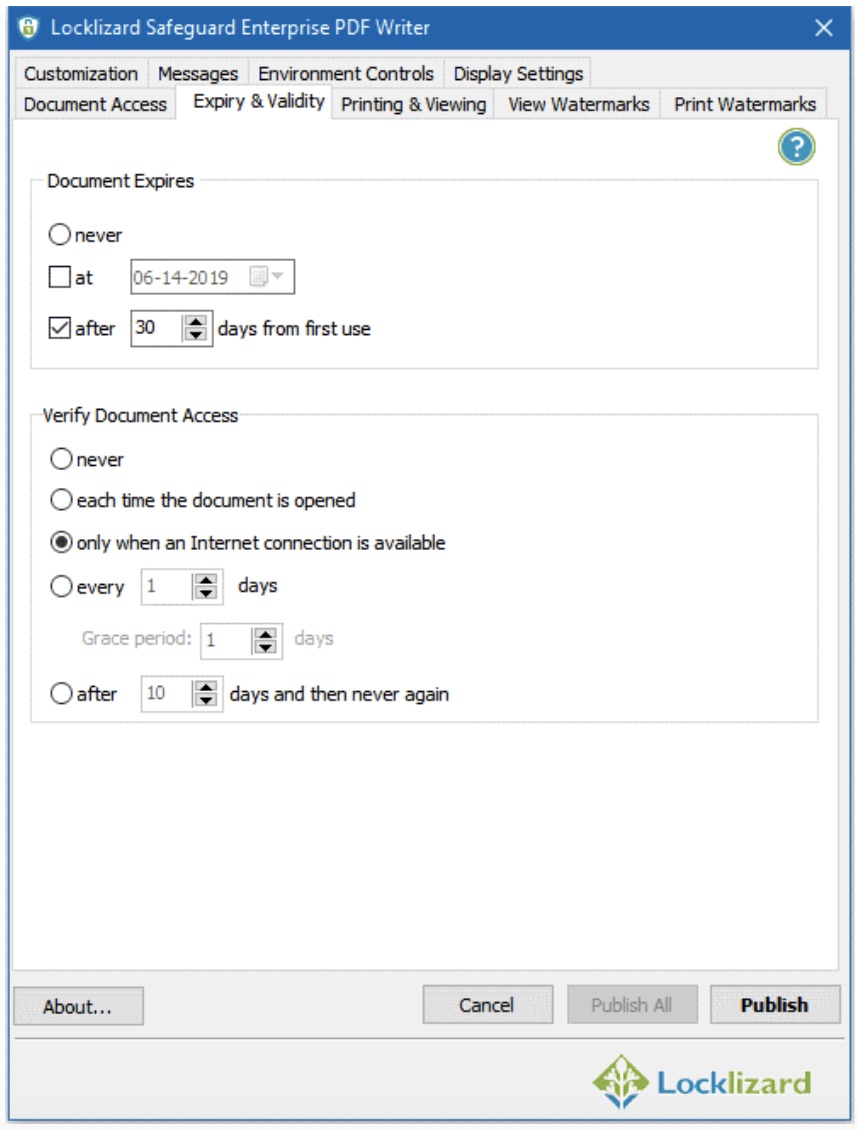
You can:
- Prevent editing and modifying of content
By default, users cannot edit and change PDF content.
- Stop copying and pasting
Copying and pasting of text and images into other applications is always prevented.
- Disable PDF printing
Printing is disabled by default.
If you want to allow users to print PDF documents, then Locklizard automatically prevent printing to file drivers such as PDF printers. This stops one of the easiest ways that can be used to create unprotected PDF documents. You can also allow only degraded printing, such as black and white or grayscale to prevent users photocopying and distributing high quality content.
- Add dynamic watermarks that display user information
Locklizard provide two main advantages of Adobe PDF watermarks or those added using PDF password protection software:
- They cannot be removed with PDF editing software
- You can insert user information dynamically
When you use Adobe Acrobat to add a PDF watermark you may not realize that it can be easily removed in a PDF editor in one single action. Locklizard create permanent watermarks that cannot be removed in PDF editing software.
You can also insert dynamic variables such as the user’s name, email, date/time, etc. which are replaced by actual data when the PDF document is viewed or printed. This has the advantage in that you only have to protect a single PDF file rather than one for each user in order to customize it. If you allow printing, it also helps to discourage users distributing printed copies since they can be readily identified as the source.
- Stop screen grabbing
An easy way for users to copy content is to take screen shots using screen grabbing tools. Many screen grabbing tools can automatically create high quality screenshots and save them in a single file or PDF document. Locklizard prevents all screen grabbers from grabbing images of PDF content so that at best users can only take photos of their screen using their mobile phones.
- Prevent saving to unprotected file formats
Users cannot save protected PDF files to unprotected formats – there is no option in the secure viewer to save files.
- Expire PDF files
PDF files can be set to expire after:
- a number of days after they are opened
- a number of views (opens)
- a number of prints
- on a specific date
You can set the same PDF file to expire on a specific date that is the same for all users or different dates for different users by adjusting this on the Safeguard Admin System. The number of days, views and prints expiry is allocated to each user so that if you set a PDF to expire after 3 days, then each user has 3 days to view it from the date they first open it. Expiry controls can be used in combination with each other, so whatever comes first triggers the PDF file to expire.
- Lock PDF files to devices
Being able to lock PDF files to devices or machines is a fundamental control in preventing sharing of PDF documents. This is because if a PDF document is copied to another device it will not open – it needs the correct key to decrypt it and that key will only work on the device it has been locked to. So unlike passwords that can be shared along with the protected PDF file, Locklizard ensures that only devices that have been authorized can open encrypted PDFs.
- Lock PDF files to country and IP locations
With BYOD it is hard to control where users can view your confidential and sensitive documents. Locklizard however have this in hand by enabling you to lock use to specific locations. For example, you can prevent users opening protected PDF documents outside of the office, or control the locations third parties can use them from.
- Track PDF opens and prints
For accountability or compliance reasons, you might want to see what users have opened and printed your PDF documents and when this took place. Locklizard enable you to do this seamlessly, tracking both document open and print activity.
- Instantly revoke documents and users
Another great feature of Locklizard is the ability to instantly revoke both users and documents. Once a user has been revoked, they cannot open any documents, and once a document has been revoked no one can open it. It does not matter where the documents are located since they are checked when an open request is made.
Secure PDF Readers
Locklizard provides dedicated PDF Viewer applications that have been built specifically for security and do not allow JavaScript or external plugins. This has the added benefit of enabling document viewing even when a user is offline, which is vital in some industries.
PDF files can also be protected to USB devices along with a secure Viewer so that users can instantly view protected PDF files on the device without having to install any software.
And lastly, they provide a Web Viewer so users can view protected PDF files in their browser.
Secure Document Distribution
With Locklizard you protect PDF files on your computer (so you don’t have to upload unprotected files to a third-party cloud server) and you distribute them just like any other file. Only users that you give access to via the Safeguard Admin System can open them, so it does not matter where these protected PDF files are stored or who can access them.
When you create a user on the Safeguard Admin System (you enter their name and email address and optionally a company name), it sends that user an email. This contains a link to the secure Viewer software and a license file link. Users install the secure Viewer and then click on their license link to activate it. Once they have done that, they can view any protected PDF files you have given them access to.
Giving a user access to a protected PDF file is as simple as selecting it on the Safeguard Admin System and choosing the user(s) who can access it.
The system is extremely easy to use and can be enhanced with additional modules such as PDF batch protection and ecommerce integration for automated processing of PDF files and users.
Conclusion: what is the best PDF protection software?
The bottom line, then, is this: for the organization that’s looking to protect internal and external PDF documents, a PDF DRM system is the best solution to protect PDF files. It may be tempting to go for low-cost PDF password protection solutions or be tricked by secure data room marketing, but ultimately money spent on an ineffective solution is wasted money.
To that end, Locklizard Safeguard is the best PDF protection on the market today, enabling you to securely share and sell PDF documents without the worries of them being easily leaked or pirated.
Learn more about Locklizard DRM Copy Protection Software for Documents, Files and Ebooks
Advertising disclosure: We may receive compensation for some of the links in our stories. Thank you for supporting LA Weekly and our advertisers.
